Cybersecurity & Back up Information
 We have over 20 years of researching of new technologies such as cybersecurity, which allow us provide the safest solutions to protect the information of our clients from cyber attacks, Phishing. That's the reason the corporations take actions in this topic worldwide to keep your information safe.
We have over 20 years of researching of new technologies such as cybersecurity, which allow us provide the safest solutions to protect the information of our clients from cyber attacks, Phishing. That's the reason the corporations take actions in this topic worldwide to keep your information safe.
Installation of Firewall and security in Computer Equipment and Networks
Implementation of firewalls...
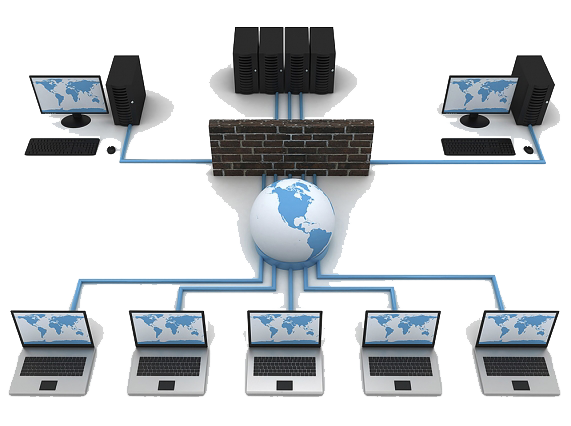
A firewall is a part of a system or network that is designed to block unauthorized access while allowing authorized communications.
It is a device or set of devices configured to allow, limit, encrypt, decrypt, traffic between different domains based on a set of rules and other criteria.
Firewalls can be implemented in hardware or software, or a combination of both. Firewalls are often used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets.
All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet specified security criteria. It is also common to connect the firewall to a third network, called the "demilitarized zone" or DMZ, in which the organization's servers are located that must remain accessible from the outside network.
A properly configured firewall adds necessary protection to the network, but in no case should it be considered sufficient. Computer security covers more areas and more levels of work and protection. More measures can be added such as content filtering, detection and/or protection against other types of intruders, such as different types of malware, antivirus, etc.
Benefits that could be obtained:
A firewall is like a bottleneck that all incoming and outgoing Internet traffic must pass through, allowing you to control the traffic. A good, well-configured and managed firewall greatly prevents hackers from getting past it and of course helps you keep your company's sensitive data safe. In this sense, a firewall:
a. It works as a gateway with controlled access for each information packet that travels from outside to our network and vice versa.
b. It monitors and records the services used to use the Internet, FTP and other protocols.
c. Allows you to define a “barrier” keeping unauthorized users aside.
d. Prevention of attacks on your private network from other external networks.
and. Control the security of your network and individual computers when any suspicious activity occurs.
F. Control of Internet usage by blocking or unblocking inappropriate or appropriate ports (IP, TCP, SSL, UDP, etc.).
Information Backup Systems
Do you know if your information is protected correctly?
Does your company have effective security systems that allow you to stop an attack or computer infiltration?
Did you know that there are tools that allow you to know what is the information traffic that circulates in your network?
Does your company have a system that allows you to control your network traffic and efficiently limit access to unwanted sites or places, maximizing the working time of your staff?
Does your company have an adequate backup system?
During years of research we have corroborated, and from our own experience, that Hackers concentrate attacks on end users of mail and networks that are not adequately protected, many users believe that having their device equipped with an antivirus system will completely secure the information on this and unfortunately they are wrong, these often only protect against possible threats and not against infiltrations!

That is why we offer efficient backup insurance systems that will allow you to protect your information that will maximize the security of your company, with a redundancy of benefits that were unprecedented until now and that your company or company cannot wait any longer!
Contact us and we will gladly schedule a visit in search of solving your technical problems


